3 Common Red Team Mistakes Tipping off SOC and Threat Hunters Instantly

From the defender’s side, spotting an intrusion often isn’t about reversing a high-end exploit but rather about recognising mistake patterns attackers make when performing intrusive actions.
Modern EDR and logging pipelines turn small missteps into clear signals, allowing SOC teams and threat hunters to connect the dots fast. This post highlights the most common pitfalls, and what both attackers and defenders can learn from them.
Noisy Enumeration That Lights Up Telemetry
One of the quickest ways attackers reveal themselves is through loud, broad enumeration. Aggressive Nmap sweeps, SMB probes, wide LDAP queries, and rapid-fire service discovery/directory bruteforcing might work in isolated labs, but in monitored environments they create an unmistakable signature.
Network scanners trip lateral-movement rules, EDR flags unusual discovery behaviors, and SIEM dashboards light up with correlation alerts. To defenders, this kind of activity is the equivalent of lighting a flare in a dark room: attention-grabbing and easy to trace. Quiet reconnaissance requires planning, restraint, and an understanding of how every action appears in telemetry, not just whether it succeeds technically.

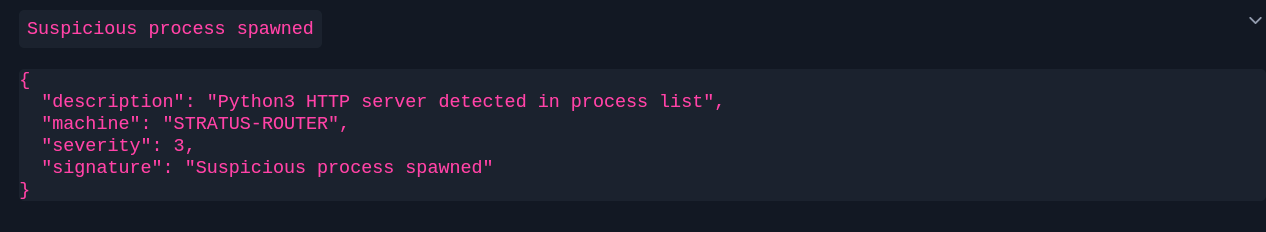
Suspicious Process Trees and Parent/Child Relationships
Even when attackers keep their network noise low, their process behavior often gives them away. Launching PowerShell from Office applications, spawning winPEAS.exe, or chaining tools in combinations that don’t occur during normal user activity creates immediate red flags in modern EDR platforms.
Defenders rely heavily on process-tree context, not just the commands themselves, to understand how an intrusion unfolds. A single odd parent-child relationship can expose the entire operation: one malformed chain tells the story of an attacker improvising inside a system they don’t fully control. It stresses the need for the ability to think in terms of context, not just execution.
Poor Infrastructure Management
Infrastructure mistakes are one of the easiest ways for defenders to identify an attacker long before any beacon executes its first task. Misconfigured C2 servers, default ports, missing redirectors, DNS patterns, insufficient domain credibility all create highly recognisable signals in modern detection pipelines.
Outbound traffic that repeatedly calls home to a single IP on fixed intervals, known malicious TLS fingerprints etc. can expose the operator’s foothold immediately. While labs often abstract this complexity away, real environments treat offensive infrastructure hygiene as a first-class indicator of red team quality. Skilled operators know that their infra communicates long before defenders do.
Conclusion
These mistakes all stem from the same core issue: most training environments don’t reflect how real networks see and interpret attacker behaviour. Whether you're on offense or defense, understanding how telemetry exposes tradecraft is essential to successful client engagements.
Written by the TraceHunt team as part of our effort to bring more realistic, OPSEC-aware training to the community.



